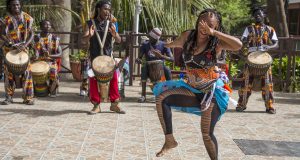Apollo får charter til Gambia, der frem til pandemien næsten konstant var Spies-rejsemål. ”Good luck til Apollo, men vi har ikke stor nok efterspørgsel til at få charterfly til Gambia,” siger Spies. | ![]()
-
Spies: Vi har ikke stor efterspørgsel efter Gambia
-
Udviklingen ventes drevet af data og nye tendenser
Data spiller en stadig vigtigere rolle i biludlejning, fortæller OAG, der samtidig peger på tre nye tendenser, som man regner med vil have indflydelse på branchens udvikling i de kommende år. |
Læs Mere »
Sponsor
-
Rejsebureauforening undrer sig over banks ferieråd
Spar Nord-banken har flere ferieråd til forbrugerne. Danmarks Rejsebureau Forenings direktør undrer sig over, at man ikke nævner muligheden for at købe hos en danskregistreret rejsearrangør. |
Læs Mere »
-
SAS-fly med business class på charter til Gambia
Apollo åbner på Gambia – det ugentlige SAS-fly fra København har tre kabineklasser: Standard, Plus og Business. ”Vi har søgt rejsemål der var kendt på det danske marked,” siger Apollo-direktør. |
Læs Mere »
-
Året starter med millionunderskud hos Scandic
De første tre måneder af Scandic Hotels' 2024 endte med et negativt resultat, der blev 25 millioner svenske kroner større end i samme periode sidste år. De danske hoteller havde højest belægning. |
Læs Mere »
-
Kendt rejsemål beder turisterne spare på vandet
Algarve-kysten i det sydlige Portugal, ét af danskernes mest besøgte rejsemål i landet, har iværksat kampagne for at få turisterne til at reducere vandforbruget. ”Beskyt fremtiden,” lyder det.
Læs Mere »
Luftfart
-
USA’s rejsebureauforening: Sur på American Airlines
American Airlines åbner til juni daglig rute til København. På sin hjemmebane får AA hård kritik. American har ingen nordisk repræsentant og har ”opsagt kontrakter med nordiske rejsebureauer.” |
Læs Mere »
-
Icelandair i nyt samarbejde med Expedia
-
Dansk højesteretsdom kan påvirke salg af flybilletter |

-
Danskerne klager dagligt over flyselskaber
Hoteller
-
Endnu en international hotelkæde skifter navn
NH Hotel Group, som er en del af Minor Hotels og hotelkoncernen bag det femstjernede hotel NH Collection Copenhagen, vil fremover drive hoteller under navnet Minor Hotels Europe & Americas.
Læs Mere » -
Ny aftale fordobler hotelkoncern i Tyskland
-
Delvis dansk hotelkæde får fjerde hotel i Schweiz
-
Hotelgigant fortsætter global ekspansion
Erhvervsrejser
-
Her er de erhvervsrejsendes mest besøgte rejsemål
Erhvervsrejsekoncernen BCD Travel har opgjort hvilke rejsemål i og uden for Europa firmakunder rejste mest til sidste år. I Europa var det Amsterdam – ud af Europa var New York topscorer. |
Læs Mere »
-
Amex-køb kan styrke mindre erhvervsrejsebureauer |

-
Amex GBT overtager CWT
-
Kun et rejsebureau udstillede på stor mødemesse |

Teknologi
-
Slår rekord: Sletter falske anmeldelser som aldrig før
Tripadvisor har nu fjernet omkring 6,5 procent af de anmeldelser, der blev lavet på sitet sidste år, da det har vist sig, at de enten var usande eller afgivet under falske forudsætninger. |
Læs Mere »
-
Hotelsoftware kan stå i vejen for fri konkurrence |

-
Fransk søgemaskine gør sit indtog i Danmark |

-
Stena Line-rejsebureau lancerer kunstig intelligens |

Rejsebureauer
-
Stadig flere klager til Pakkerejse-Ankenævnet
Pakkerejse-Ankenævnet modtog sidste år 299 klagesager fra rejsekunder, en stigning på 51 procent i forhold til 2022. I alt blev 99 sager sidste år afgjort i selve Pakkerejse-Ankenævnet. |
Læs Mere »
-
Kilroys koncernvækst drevet af det danske marked |

-
Rejsebureau konkurs: Kunne ikke betale coronalån |

-
Præsenterede udspil til ny rejsemesse i København |

Turisme i udlandet
-
Amsterdam klar med nye tiltag til turistreduktion
Bystyret i Amsterdam vil i indsatsen mod overturisme have færre turister. Det skal nu også gælde flodkrydstogtskibe – anløb af disse skal halveres og skibene skal opfylde krav om landstrøm.
Læs Mere » -
Taylor Swift udløser rejseboom til Stockholm |

-
Første østrigske region får Østrigs miljømærke
-
Alternativ lufthavn giver rejsearrangør salgsboom |

Biludlejning
-
Endnu en biludlejningsgigant reducerer antal elbiler
I lighed med andre globale biludlejningskoncerner, beskærer nu også den tyske mastodont Sixt antallet af elbiler til udlejning. Efterspørgslen falder og brugtvognsprisen er svigtende, lyder det. |
Læs Mere »
-
Prisen på udlejningsbiler falder på kendte rejsemål |

-
Biludlejningskæmpe bestiller 250.000 nye køretøjer |

-
Biludlejningsgigant dropper 20.000 elbiler |

Jernbane
-
Deutsche Bahn på vej med private kupéer i fjerntog
Rejser med fjerntog er stort i Tyskland, også for forretningsfolk. For at tilbyde mere privatliv til for eksempel telefonsamtaler eller videokonferencer, er Deutsche Bahn på vej med minikupéer. |
Læs Mere »
-
Ny togrute mellem Stockholm og København
-
Oplever boom i udlandsrejser med tyske fjerntog
-
Nyt europæisk nattog kører nu også til Prag
Rederier
-
Rederi åbner ny passagerrute fra Malmø til Polen
Finnlines, det italienskejede fragt- og passagerrederi, åbner med kort varsel ny daglig færgerute fra Malmø til den polske havneby Swinoujscie. Skibet på ruten har plads til 440 passagerer.
Læs Mere » -
Sænker pris på færgeafgange med lav efterspørgsel |

-
Udbud på vej: DFDS overvejer at byde |

-
Færgerederi øger på Danmark og får ny norsk rute
Krydstogt
-
Luksuskrydstogtskib får usædvanlige gudforældre
Normalt får krydstogtskibe film- og musikstjerner eller bestyrelsesformandens hustru som gudmor. Men når Seabourn Pursuit officielt navngives, er der valgt en stamme fra Australien.
Læs Mere » -
Sir Richard uddelte 200 gratis krydstogter
-
Større lufthavne styrker Grønlands krydstogtturisme
-
Repræsentationsbureau får tredje krydstogtkunde |

Navnenyt
-
40-års jubilæum: Skulle kun have været guide i ét år
”Man skal være ydmyg over for, hvor mange penge, gæsterne har til deres rejse,” siger 40-års jubilar hos Spies, Lone Alstrup. Spies' direktør: ”Lone er virkelig en ambassadør for vores værdier."
Læs Mere » -
Kendt luksuskrydstogtrederi skifter uventet topchef |

-
Spies-ejer justerer bestyrelser hos sine turoperatører |

-
Stopper som rejsebureaudirektør – og DRF-formand |

Bagsiden
-
Aprilsnar: Rejsebranchen var igen leveringsdygtig
Arp-Hansen, Cirkusbygningen, Destination Nordvestkysten, MyCruise, Strawberry, Tivoli Friheden, Travelport, TUI og Østrigs jernbaner var blandt de mange der 1. april havde ikke-holdbare nyheder. |
Læs Mere »
-
Projektchefen må i år se Ferie for Alle fra en kørestol
-
Sverige uddelte sine årlige Grand Travel Awards |

-
Rejsebranchen støttede Danmarks Indsamlingen
Ung i rejsebranchen
-
“Jeg elsker at udvikle mig og tage nye udfordringer”
27-årige Sara Matras begyndte som rejseleder i Spies. I dag er hun på hovedkontoret og ansvarlig for den digitale service i udlandet og en del af uddannelsesforløbet af nyt udlandspersonale |
Læs Mere »
-
“Min far havde en landingsbane i baghaven” |

-
”Øget fokus på miljø lægger større pres på os i rejsebranchen” |

-
”Vi skal tænke lidt mere på hinanden og vores planet” |

7´eren
-
“Jeg er vokset med opgaven”
Den 35-årige Kristoffer Sundberg er øverste chef i Billund-flyselskabet SUN-AIR, der årligt omsætter for en halv milliard kroner. Snart skal der tages beslutning om ny flytype til flåden. |
Læs Mere »
-
Aller Leisure: ”Rejsebranchen er både ukuelig og umoden” |

-
“Vi skal have et relevant, moderne og attraktivt produkt” |

-
“Jeg troede på projektet” |


 STANDBY.DK Nyt om rejser
STANDBY.DK Nyt om rejser